Whether you are new to the field or well-seasoned, it is important to understand how data is transmitted across our networks. The Open Systems Interconnect (OSI) model and TCP/IP suite are networking models that provide a framework on that process. While the OSI model is heavily emphasized in A+ and Network+, it’s often said that our networks predominantly run on the TCP/IP model. You’ve probably come across job descriptions that require a basic understanding of TCP/IP but often overlook the OSI model. Is there a difference between the two models, and does it matter?
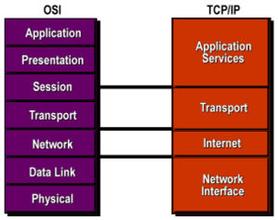
OSI Model: Network Foundations
Before the OSI model, devices lacked a standardized way to communicate. Introduced in the 1980s, it defined network communication into seven layers, each with a specific function.
It is helpful to remember for what it is - not as gospel, but as a point of reference that allows us to have an idea of how networks flow. Not every protocol nor piece of hardware or software will seamlessly fit in these layers. Yet what are the layers?
Application Layer
Whenever you surf the web, send an e-mail, or remotely connect into a switch, you are interacting with the application layer. This layer is our level of interaction. Applications refer to software that serve as underlying services to the greater program. For example, surfing the web on Chrome utilizes HTTP/HTTPS, which are application-layer protocols.
Presentation Layer
This layer is all about image. Data is presented in a way that we can understand and secure. Secure web browsing (HTTPS) uses TLS, an encryption protocol. It also handles file formatting and compression. If you are sending a Word document with accented words, such as touché, text is represented as UTF-8 encoding. If you are sending this document to a device that supports only ASCII, an older version to UTF-8, you may only see touche, with no tilde over the e. The Presentation layer is responsible for such conversations.
Session Layer
The Session Layer is responsible for establishing, maintaining, and terminating communication between two devices. For example, if you are shopping online, the session layer is in action. A session is created when you access the site. You gain a session ID; web sessions are maintained using that session ID for every request made as a form of tracking. The session is closed when you are done shopping and close the tab.
Transport Layer
The Transport Layer handles communication between hosts using two main protocols: TCP and UDP. TCP ensures reliable data transfer, error checking, and congestion control, using a three-way handshake to establish connections. In contrast, UDP is faster with less overhead but doesn't guarantee reliability, offering basic error checking instead.
Accessing the web? You are utilizing a TCP protocol: HTTPS. When you do a videoconference or streaming, you are utilizing a UDP protocol: RTP. What if you are watching a live stream on YouTube? Personally, it struck me that we can watch live TV over a HTTPS connection. How is it mostly so smooth? What is being used here? There is another transport layer protocol: QUIC. QUIC, or Quick UDP Internet Connections, is a protocol designed to improve overhead on real-time services, such as video streaming, that use a TCP connection. QUIC is built on UDP but provides some services of TCP, such as reliable data transfer.
To learn more about the QUIC protocol, read here.
Network Layer
The Network Layer is responsible for routing packets between hosts using logical addresses called IP addresses and routing protocols. It communicates layer 3 information via protocols like ICMP. For example, whenever you ping a website or IP address, you are using ICMP. Unlike the Transport Layer, it offers no error checking and uses a "best effort" service, meaning packets may arrive out of order or get lost. For instance, when sending a document, packets may take different routes, and some pieces could be missing upon arrival. Talk about lost in translation!
Data Link Layer
The Data Link Layer formats data into frames for local transmissions, using MAC addresses - unique physical addresses on network cards - for communication. Unlike the Network Layer's logical addresses, MAC addresses are physical and crucial for devices like switches, bridges, and access points within a LAN. This layer handles Ethernet and Wi-Fi and uses ARP to map IP addresses to MAC addresses. Errors in ARP can cause delays by sending frames to incorrect MAC addresses. Additionally, LANs can be segmented into VLANs, which also operate at this layer.
ARP is a data link layer protocol used within LANs to develop an ARP table for individual hosts. PC2 pings all the PCs within the LAN and the DHCP server. The MAC address and IP address for each of those devices are mapped within the PC's ARP table.
Physical Layer
This layer makes up the bare bones, our highways, foundation - whatever you want to call it - of our network. This where raw data in the form of bits are transmitted. Wired media include Ethernet cabling, coaxial cabling, and fiber optics. Wireless media include radio transmissions via Wi-Fi, Bluetooth, or radio frequencies.
TCP/IP Model: Backbone of Today's Network
While the OSI model has more layers, not all are equally relevant in practice. For instance, a laptop connects via Wi-Fi (Layer 1) through an access point (Layer 2) to a router (Layer 3). A firewall (Layer 4 or 7) may then filter traffic based on protocols. While the other layers clearly map to hardware or software, the session and presentation layers are a bit harder to visualize in real-world applications.
The TCP/IP model predates the OSI model. In the 1970s, the Defense Advanced Research Projects Agency (DARPA) formulated the model for the Internet's predecessor - ARPANET. Yet, it is more practical and used in real-world applications. It is very similar to the OSI model. Unlike 7 layers, there are 4 or 5 layers, depending on how it is broken up.
Application Layer
This layer combines the session, presentation, and application layers of the OSI model, handling communication between devices like laptops, servers, and smartphones. This is where data begins in its transit.
Security Considerations:
- Open Ports: Unused open ports can be a security risk. Use a port scanner to find them and a firewall to control access.
- Access Control: Set up ACLs correctly to allow only necessary traffic.
- DNS Issues: Problems with domain resolution can arise. Check DNS settings, the hosts file, and use tools like
nslookupordigto troubleshoot.
Transport Layer
This layer performs the same function as the transport layer in the OSI model, handling host-to-host communication and ensuring data reaches its destination. It formats data into segments and includes devices like firewalls and load balancers for managing traffic and congestion.
Common Issues:
Transport layer issues like packet loss or connection timeouts can often happen due to network congestion. For example, if you use are on a videoconference call and experience frequent drops throughout, optimize your network performance by:
- Consider your network bandwidth and throughput.
- Configure Quality of Service. Prioritize real-time communication over loss-tolerant communication, such as web browsing or e-mail. Reduce other activities that can take up bandwidth space while you are on the call, such as TV streaming or downloading big files.
Network Layer
Like the OSI network layer, this layer focuses on sending packets between hosts on different networks and routing them efficiently. At this layer, you will find routers and multilayer switches. Those segments are formatted and packaged into packets, ready to move on to the next layer.
Common issues existing within the network layer include IP address conflicts and routing loops. For example, a /24 network can have at maximum 254 hosts that can receive an IP address. If a person decided to connect to the network but cannot, this may be due to address space exhaustion or a duplicate IP address. Routing loops occur when data circulates endlessly due to incorrect routing or slow protocol convergence.
- IP Address Conflicts: Configure DHCP to assign unique IP addresses within an allotted scope. Check your subnet designs for adequate space for the number of devices that can fit the network. Manually putting in IP addresses for devices can lead to errors and duplicate IP addresses.
- Routing loops: Check routing tables. Implement loop-prevention techniques such as route poisoning (marking a down route as unreachable or "infinite"), split horizon (telling other routers that a certain route is down and do not take it), or assign a Time-to-Live limit (the maximum amount of routers a packet can travel before discarding it).
Network Interface Layer
The network interface layer merges the OSI model’s data link and physical layers, formatting packets into frames for transmission over wired or wireless media. Switches and bridges operate at this layer, while the physical layer deals with transmission media and hardware.
Common Issues & Fixes:
- Switching Loops: Prevent with Spanning Tree Protocol (STP) to block redundant paths.
- VLAN Misconfigurations: Ensure correct host placement and properly configured VLAN trunks.
- Loose Cabling: Secure connections to avoid dropped signals and slow speeds.
- Duplex Mismatch: Match duplex settings on both devices or set them to auto for proper communication.

Signed, Sealed, Delivered: Encapsulation and De-encapsulation

Whether it is the OSI model or the TCP/IP model, both describe how network transmit and formats bits into the data that we receive in applications. There is a sending side and a receiving side. On the sender's side, encapsulation wraps data in headers and trailers, while on the receiver's side, de-encapsulation removes them. Encapsulation is the process of adding headers and trailers as you go down the protocols, from application to the network interface. De-encapsulation is the process of removing headers and trailers as you go up the protocols, from network interface to application. This two-way process is often compared to how our mail is delivered. Let's walk through the process:
1) Application Layer: First, you write a letter. Just as how the letter has all the contents in it, a webpage or an e-mail will have contents, or data, that will be transferred to its destination. Just as you probably won't just send the paper letter by itself in the mail, these application-layer processes need to be properly "enveloped" for transmission.
2) Transport Layer: To do that, that letter is then stuffed into an envelope. Encapsulation involves adding headers, which is extra information that helps guide data to its destination. An envelope also provides security; when it is time for collection, your letter is safe from roaming eyes (without opening) when it is in envelope. The transport layer provides services to the application layer, such as reliable data transfer.
3) Network Layer: Then, you write a return and a destination address. The source and destination IP address is helpful in routing packets to where it needs to go. Transport-layer data called segments - including source and destination port numbers - become encapsulated with these IP addresses.
4) Network Interface Layer: After writing the addresses and stamping it, you drop off the letter at your mailbox. The postal service is then responsible to ship your letter to the appropriate address. If we are breaking up this layer, dropping off the letter for the postal service to deliver would be the link layer. Just before it reaches the physical medium, these packets are encapsulated into frames, which tack on additional headers. The actual delivery process - driving, walking, opening mailboxes - would represent the physical layer. This would describe any wiring or wireless methods the bits would travel over.
5) De-encapsulation: Once it arrives at its destination, the recipient sees that it is addressed for them, open the envelope, and takes out the letter for them to read. At this point, the process goes in reverse. Instead of tacking on headers, these are stripped until the data reaches the host at the application layer. This is called de-encapsulation.
What's the Verdict?
| OSI and TCP/IP Model Comparison | |||
|---|---|---|---|
| OSI | TCP/IP | Functions | Protocols |
| Application | Application | Allows for inter-process communication between end hosts and protocols to format and interpret data and set up connections between end hosts |
HTTPS/HTTP, IMAP, RDP, DNS |
| Presentation | ASCII, SSL, .JPG, .PNG, .MP4, .DOCX | ||
| Session | PPTP, RPCP | ||
| Transport | Transport | Host-to-host communication amongst processes, ensuring data reaches its destination host | TCP, UDP |
| Network | Network | Sending packets between hosts on different networks and routing them efficiently | IP, ICMP |
| Data Link | Network Interface | Formatting packets into frames for transmission between connected devices within the same physical network | MAC, Ethernet, 802.11, ARP |
| Physical | Physical transmission of raw data in the form of bits over a medium | Cabling, Ethernet, 802.11 | |
The OSI model and TCP/IP suite have been helpful tools to understand how our networks are broken down and the functions they serve. You might find that not all the layers are commonly used for network professionals. The TCP/IP suite keeps our networks going. After all, two fundamental protocols are mentioned in the name. Understanding TCP/IP can help networking professionals identify issues at certain parts of the stack and see how they all correlate to each other. The OSI reference model is often used for to teach networking fundamentals. Beyond education, why is it used? At the heart of the matter, they are both ways to understand our networks and prepare us on how to handle the hardware and software.
Take the time to understand protocols and these layers. If you do not have the physical hardware, utilize modeling labs to see how switches, routers, cabling, and other infrastructure function within networks. Even within your own homes, use Wireshark to see what traffic you got going on. Use the packet list panel to see which protocols are often implemented and the packet details panel to see the different layers of the TCP/IP suite. Mastering these models won’t just help you pass exams—it’ll make you more proficient in troubleshooting real-world networks.
What has been your experience with either model? Has it played a major role in troubleshooting network issues? What are some troubleshooting tips that help you when you face issues in your network? Feel free to share them in the comments!

Comments
Post a Comment