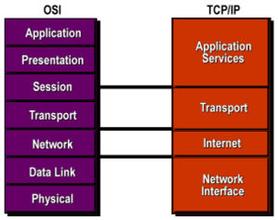
Whether you are new to IT or a seasoned admin, chances are you have heard of the OSI or the TCP/IP model. These frameworks help us understand how data flows across our networks — from online shopping to high-speed data transfers. However, many job postings require knowledge of TCP/IP but not OSI. Why is that? Is one favored over the other? Let's take a look at both.
What is the OSI Model?
| Layer | Functions |
|---|---|
| 7. Application | User and device interaction for network services (web browsing, email, file transfer) |
| 6. Presentation | Formats data for applications, ensures readable and secure data |
| 5. Session | Establishes, maintains, and ends connections between devices. For example: Online shopping uses a session ID to track your activity until you leave the site. |
| 4. Transport | Handles data delivery (e.g., TCP, UDP, QUIC, error checking) |
| 3. Network | Routes packets between hosts via IP addresses and routing protocols |
| 2. Data Link | Formats data into frames for local transfer using MAC addresses |
| 1. Physical | Transmits raw bits over wired or wireless media (e.g. copper cables, fiber optics, Wi-Fi, Bluetooth) |
How does data actually flow through these layers?

Think of it as sending a package. Each layer wraps data like putting a mug in wrapping paper, bubble wrap, then in a box, and putting a label on it. When it reaches the recipient, it's unwrapped in reverse. When you send a message, it goes from layer 7 (Application layer) to layer 1 (Physical layer), through the process called encapsulation. When you receive a message, it goes in the opposite direction (Physical to Application), through a process called de-encapsulation.
TCP/IP Model: Today's Network Backbone
| TCP/IP Layer | Corresponding OSI Layers | Functions | Common Protocols |
|---|---|---|---|
| Application | Session, Presentation, Application (5–7) | Provides services for user-facing applications, handles formatting, encryption, and connection setup between end hosts. | HTTP/S, DNS, IMAP, RDP, TLS |
| Transport | Transport (Layer 4) | Ensures reliable or fast delivery between hosts using flow control, segmentation, and error checking. | TCP, UDP, QUIC |
| Network | Network (Layer 3) | Routes packets across networks using logical addressing and routing protocols. | IP, ICMP, IGMP |
| Network Interface | Data Link (Layer 2) | Formats packets into frames for transmission within the same network and handles MAC addressing. | Ethernet, ARP, PPP, 802.11 |
| Physical (Layer 1) | Transmits raw bits over physical media like cables or wireless signals. | Fiber, Ethernet, Wi-Fi, Bluetooth |
Application Layer: Human Interaction Layer
This layer combines the session, presentation, and application layers of the OSI model. It handles process-to-process communication between devices like laptops,
servers, and smartphones. This is where protocols and services support user applications like browsers or remote desktop clients. This is not referring to apps like Google Chrome or Remmina, but their underlying services like HTTPS or RDP.
Common Protocols:
- HTTP/S (HyperText Transfer Protocol/Secure) - Insecure/secure web browsing
- DNS (Domain Name System) - Converts human-readable hostnames into machine-readable IP addresses
- IMAP (Internet Message Access Protocol) - Receives email across synced devices
- RDP (Remote Desktop Protocol) - Allows for remote connection to a device with an interactive interface on Windows
- TLS (Transport Layer Security) - Security protocol used for secure browsing
Security Considerations:
- Open Ports: Unused open ports can be a security risk. Use a port scanner to find them and a firewall to control access.
- Access Control: Set up ACLs correctly to allow only necessary traffic.
- DNS Issues: Problems with domain resolution can arise. Check DNS settings, the hosts file, and use tools like
nslookupordigto troubleshoot.
Transport Layer: (Un)Reliable Delivery?
This layer mirrors layer 4 in the OSI model. It is responsible for ensuring data gets to its destination using either of the two main protocols:
TCP (Transmission Control Protocol)
- Ensures reliable data transfer
- Performs error checking, flow control, congestion control, windowing, etc.
- Uses three-way handshake to initiate a connection for data transfer
Common Uses
- Web browsing (HTTPS)
- Sending and receiving emails (SMTP/IMAP/POP3)
- File transfer (SFTP/FTP)
UDP (User Datagram Protocol)
- Much faster with less overhead
- Connectionless — no connection established to guarantee in-order delivery
- Offers basic error checking
Common Uses
- Streaming media (Netflix, Hulu, Spotify)
- VoIP (Zoom, telephony)
- DNS & DHCP services
Common Issues
- Packet loss
- Connection timeouts
- Frequent drops in real-time connections, like videoconferencing
- Consider your network bandwidth and throughput.
- Configure Quality of Service. Prioritize real-time communication over loss-tolerant communication, such as web browsing or e-mail.
- Reduce other activities that can take up bandwidth space while you are on the call, such as TV streaming or downloading big files.
Network Layer: The Post Office Layer
Common Issues
- IP address conflicts
- Configure DHCP to assign unique IP addresses within an allotted scope.
- Check your subnet designs for adequate space for the number of devices that can fit the network.
- Manually putting in IP addresses for devices can lead to errors and duplicate IP addresses.
- Routing loops
- Check routing tables for duplicates or inconsistencies
- Implement loop-prevention techniques such as:
- Route poisoning (marking a down route as unreachable or "infinite")
- Split horizon (telling other routers that a certain route is down and do not take it)
- Assign a Time-to-Live limit (the maximum amount of routers a packet can travel before discarding it).
Network Interface Layer
The network interface layer merges the OSI model’s data link and physical layers, formatting packets into frames for transmission over wired or wireless media. Switches and bridges operate at this layer, while the physical layer deals with transmission media and hardware.
Common Issues & Fixes:
- Switching Loops: Prevent with Spanning Tree Protocol (STP) to block redundant paths.
- VLAN Misconfigurations: Ensure correct host placement and properly configured VLAN trunks.
- Loose Cabling: Secure connections to avoid dropped signals and slow speeds.
- Duplex Mismatch: Match duplex settings on both devices or set them to auto for proper communication.

What's the Verdict?
| TCP/IP (Transmission Control Protocol / Internet Protocol) Model | OSI (Open System Interconnect) Model | |
| Purpose | Practical model used in real-world applications; backbone of the Internet | Conceptual model used to understand network structure |
| Number of Layers | 4 (sometimes 5) | 7 |
| Layer Names | Application, Transport, Network (Internet), Network Interface (Network Access) | Application, Presentation, Session, Transport, Network, Data Link, Physical |
| Today's Use | Widely used in modern networks and the Internet | Used in learning and troubleshooting |
| Troubleshooting | Abstracted layer structure makes it efficient for troubleshooting | Detailed structure helps pinpoint specific network issues |
The OSI model and TCP/IP protocol suite are important frameworks to networking. While the OSI model provides a conceptual way to describe network functions, the TCP/IP suite runs the modern Internet. No matter the model, it boils down to one thing: understand each layer of a network. They a both prepare us on how to troubleshoot, design, and manage hardware and software.
Take the time to understand protocols and these layers. If you do not have the physical hardware, create a virtual lab and utilize packet analyzers, like Wireshark, to see how protocols function. Mastering these models won’t just help you pass exams—it’ll make you more proficient in troubleshooting real-world networks.
Comments
Post a Comment